When dealing with technology and digital platforms, there are increased chances for cyber-attacks and breaching of data or privacy. Therefore, to provide security to enterprises, cybersecurity and IT goes hand in hand. Businesses with strong cybersecurity systems are resilient and can operate while being under cyber threats and attacks, enabling them to safely cope with disruption, increase shareholder value, and fortify customer trust.
From employees to customers, every individual feels safe while working with resilient cyber firms because it ensures everyone's safety. When all the operations and data are migrated to the cloud, it is always a wise decision to equip them with appropriate cybersecurity.
We preempt cyberattacks by leveraging the power of artificial intelligence (AI) and machine learning techniques to collects, analyzes and correlates threat data, helping us to successfully offer the following MDR services:
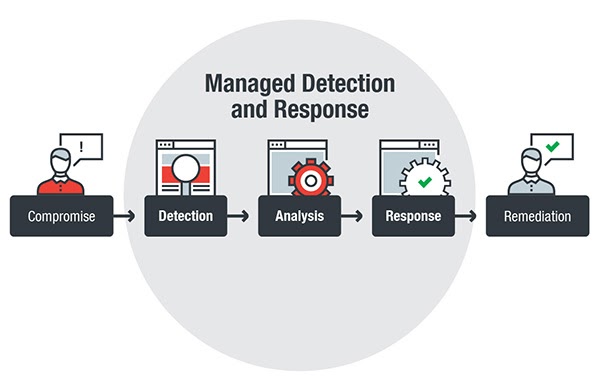
Our cyber security offering provides a holistic approach to cloud security, effectively protecting data applications and cloud system apps while ensuring regulatory requirements are met and business goals are not compromised on. Our services in the area include:
We actively look for unknown endpoint threats and respond immediately. We analyze the threats and once a threat is validated, we contain the compromised endpoints and take prompt action to protect against similar attacks in future. We offer the following services:
Our analytics-driven framework enables better contextualization to customize cyber analytics services for our clients. We integrate user and entity behavior analytics (UEBA) with third-party security information and event management (SIEM) to successfully manage investigations, automate tasks and remediate breaches. Our services in the area include:
We go beyond traditional point-in-time detection and offer innovative advanced threat protection services that promptly identify attacks and alert client organizations, enabling quick mitigation. Our offerings encompass:

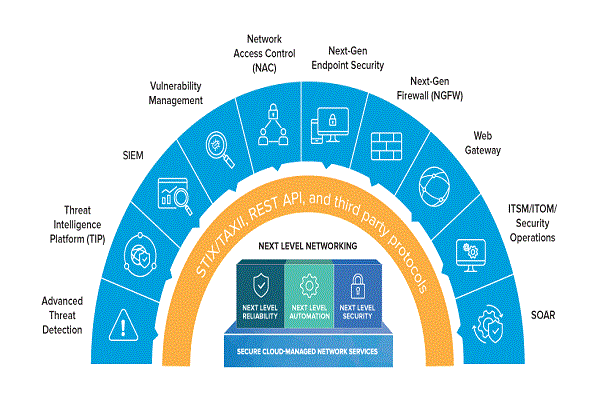
Experts at our SOC help clients leverage the latest technologies to ensure robust network security. Our services encompass:
We offer complete end to end security services for IoT platform to protect IoT devices from cyber-attacks, reducing endpoint complexity and securing its integration with CRPP:
